How to authorize an user after authenticate with Firebase
Authentication: One of the killer products on Firebase platform

Authentication will provide you an easy way to setup a login mechanism which will be up and running in short time. It has been written plenty of tutorials and demoes on how to initiate an authentication flow that will work with iOS, web og Android. And the Firebase documentation is quite good written, therefor I will not be talking about how you get started with a login.
But, and it’s important to mention, it will only handle the authentication, like how it’s named. Any good Identity platform solution (IDP) has to handle both authentication and authorization. If not, it will be very easy to hack the solution, it will also give undesirable access to anyone with a social media account, or it can give you huge problems with GDPR or similar laws.
If you read only the documentation about Firebase Auth, you won’t find anything about authorization. But if you search for “authorization” you will get more hits. For example the documentation of rules for the Realtime database mention;
“Identifying your user is only part of security. Once you know who they are, you need a way to control their access to data in your database.” https://firebase.google.com/docs/database/security#section-authorization
What is the difference between authentication and authorization?
A very short explanation: Authentication is for knowing who a user is, and authorization is what the user its allow to do. Since Firebase Auth handles different ways for only recognize the user, it will allow anyone to access your application, if you don’t complement the authentication with access control.
Do you need access control?
Yes. You will always need some sort of access control. And Firebase databases will notify you if you don’t have a minimum of access control. The minimum access control in Firebase world it will the database rules. If you don’t use access control, you will let the door open for users getting access to foreign data. For many applications the minimum level will be enough. And you don’t need roles and different level of access every time.
But if you have different use cases for the users, or different levels made for them, it will be necessary for you to handle the authorization. The rules of the database will help you a little, but you have to enhance the identity platform.
You could use a third party user and role database, and connect it with Firebase. Or you could use Firebase and define a collection of users and also combine it with the new custom claims and make a cloud function that will be the glue for the whole system.
I’m fan of using the phone number verification provided by Firebase. It is an easy way to let your users access your app without using a social media third party login. However, Firebase inform you, that if you only use phone verification and a one time password (OTP), it will not be considered safe, compared to other solutions that use multi factor authentication.
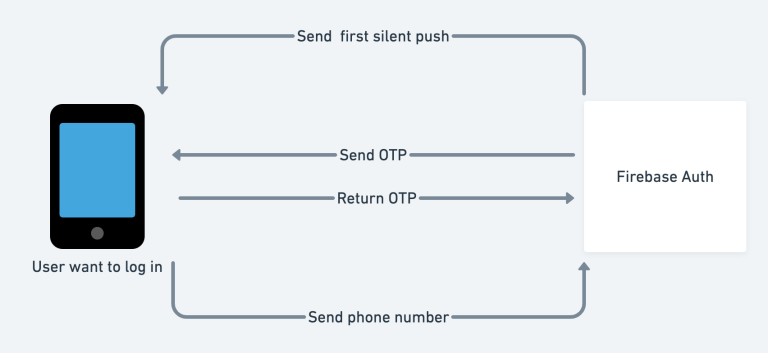
The diagram shows how Firebase deals with the phone verification. When the user wants to login to the app, it will send the phone number asking Auth for an OTP. Firebase will send a silent push to confirm that the device is requesting the OTP. After that Firebase will send the OTP and the user has to insert in the app and return it. Several step can fail, and Firebase SDK would then inform what went wrong in the code side, so that the developer can inform the user. But when the user fulfills the process, the user / device will be authenticated and the device will receive a token.
Firebase Auth will register every entry in its own database. You find the entry in the Firebase console. But the entries it not accessible, neither from the databases or from any clients. If you need to authorize the user, you have to add a user list to the database and tie it together with a cloud function.
When the Firebase Auth entry it is created or updated, it could trigger a cloud function (CF). This CF can access the user list you have available in the database and give access to the user. The cloud function can also check if the users have special claims, they should be exposed for.
.png)
If you are looking for how to handle claims take a look at Jen Personexample https://medium.com/google-developers/controlling-data-access-using-firebase-auth-custom-claims-88b3c2c9352a
When you use the Firebase Auth and with access control in the right way you will increase the security of your application without too much hassle.